To become PCI compliant, you must follow the requirements set forth by the Payment Card Industry Data Security Standards Council—an independent organization that was created by the card networks to help manage and improve payment security industry-wide.
There are 12 requirements of PCI DSS compliance—each of which falls under the scope of one of these five goals:
- Building and Maintaining a Secure Network
- Protecting Cardholder Data
- Maintaining a Program for Vulnerability Management
- Implementing Robust Access Control Policies
- Maintaining an Information Security Policy
This guide covers what each requirement means and action steps for each of the 12 requirements so you can become PCI compliant and maintain payment compliance.
Build and Maintain a Secure Network and Systems
The first two requirements are focused on preventing hackers and criminals from accessing payment systems virtually. This lowers the risk of cardholder data and sensitive authentication data falling into the wrong hands.
Requirement 1: Install and Maintain a Firewall to Protect Cardholder Data
Firewalls help control traffic that flows in and out of an organization’s network. They can be installed on routers, hardware, software, and any networking technology that’s associated with cardholder data.
- Add firewall and router configuration standards and go through formal testing whenever those configurations change.
- Make sure the configurations restrict all inbound and outbound traffic from untrusted networks and hosts.
- Prevent public access to any system components in the cardholder data environment.
- Install firewalls or software with equivalent functions on any device that’s used to access cardholder data, even when it’s outside of the organization’s network.
- Make sure all security and operational policies are documented and known to everyone who uses those systems.
Requirement 2: Don’t Use Vendor-Supplied Defaults for Passwords and Security Parameters
Hackers and scammers can exploit vulnerabilities in your network through default passwords or other default system settings in your payment infrastructure. So if you don’t change those settings after the initial deployment of your system, your payments infrastructure might be at risk.
- Change all default passwords and settings from vendors before installing payment systems on your network—including devices used to process or transmit cardholder data.
- Create configuration standards for every system component to address vulnerabilities.
- Encrypt administrative access away from the console.
- Maintain a full inventory of your system components that are in the scope of PCI DSS.
- Ensure shared hosting providers are protecting your organization’s hosting environment for cardholder data.
Protect Cardholder Data
Cardholder data refers to anything that can personally identify the cardholder or account associated with the card. The next two requirements focus on protecting cardholder data while it’s being stored or transmitted.
Requirement 3: Protect Cardholder Data in Storage
Cardholder data should never be stored unless the storage of that information is necessary for business use. Sensitive data on a chip or magnetic stripe cannot be stored after authentication.
- Limit the storage of cardholder data to only what’s legal and necessary for your business (as documented in your company’s data retention policy).
- Delete all unnecessary data at least once per quarter.
- Don’t store sensitive authentication details, even if they’re encrypted.
- Hide PAN (primary account number) data so that only authorized people can see either the first six digits or the last four digits.
- Make sure PAN data is unreadable anywhere it’s stored.
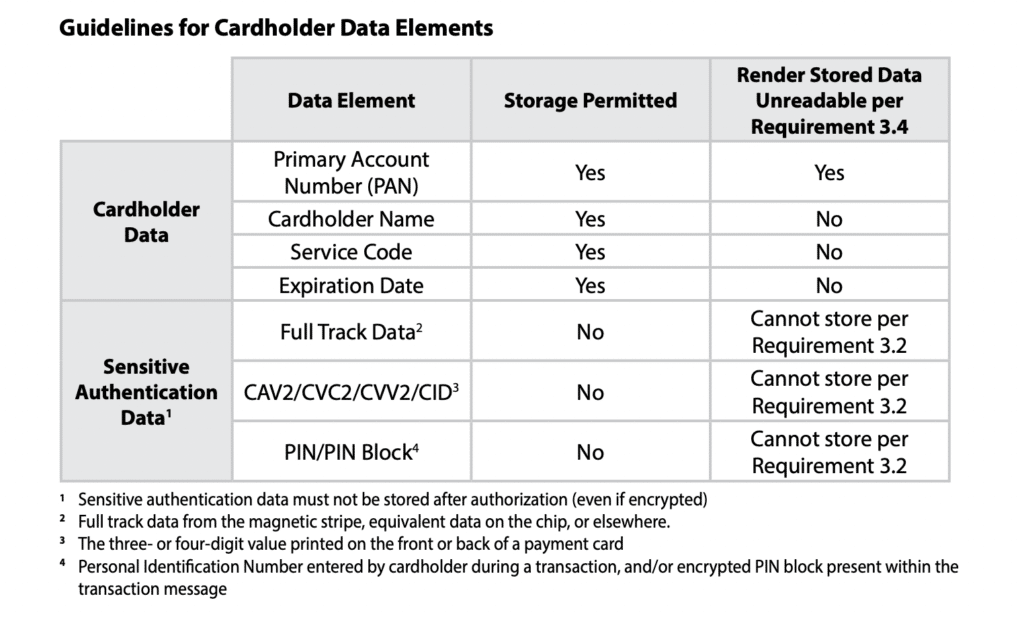
Here’s a table directly from the PCI DSS showing guidelines for different cardholder data elements:
Requirement 4: Encrypt Cardholder Data When It’s Transmitted Through Open Public Networks
If data gets transmitted through open public networks, it can be intercepted by cyber criminals. So you need to prevent those people from viewing that data while it’s being transmitted by any unauthorized users.
- Apply strong security protocols and cryptography whenever cardholder data is transmitted through open public networks, such as the internet, cellular technology, satellite communications, wireless technology, and more.
- Make sure all wireless technologies connected to the cardholder data environment use industry best practices for authentication, transmission, and encryption.
- Never send unprotected PANs through messaging platforms like email, SMS, or live chat.
Maintain a Vulnerability Management Program
Vulnerability management involves the constant effort to find weaknesses in your payment acceptance infrastructure. It involves procedures, system design, and other internal controls that could potentially be exploited or violate your system’s security policies.
Requirement 5: Protect All Systems From Malware and Update Antivirus Software
Use antivirus systems and malware protection software to protect all systems from current and evolving security threats.
- Install antivirus software on all systems that could be affected by malicious software attacks.
- Make sure that your antivirus systems are kept up to date, perform scans, and generate audit logs that are retained on file.
- Ensure antivirus systems are actively running and cannot be disabled by unauthorized personnel.
Requirement 6: Develop and Maintain Secure Systems and Applications
If your systems and apps have security vulnerabilities, then cyber criminals may be able to access cardholder data. These can typically be hardened through security patching, which quickly repairs programming code based on new threats.
- Create and maintain a process to identify vulnerabilities in your security system.
- Assign a ranking to newly discovered threats—such as high, low, or medium.
- Protect all systems from known vulnerabilities and threats by installing vendor-supplied security patches.
- Make sure all critical vulnerabilities are patched within a month of release.
- Make sure all internal and external software applications (including web-based apps) are developed in accordance with PCI DSS.
- Ensure developers are properly trained on secure coding guidelines and how to handle sensitive data.
- Make sure all publicly-facing web apps are hardened against known attacks.
Implement Strong Access Control Policies
An access control system allows businesses to either permit or deny the access to cardholder data—granted on a need-to-know basis. This includes computer files, cloud files, or physical records.
Requirement 7: Restrict Access to Cardholder Data
You must ensure that sensitive data can only be accessed by authorized users based on their job responsibility or “need to know” authority. In simple terms, this means that users are only granted the least amount of data that they need to perform a specific job.
- Limit access to cardholder data and sensitive system components only to people who need that information for their job.
- Create an access control system for components that restricts users based on what they need to know, and should be set to “deny all” unless specifically allowed by the user’s role.
Requirement 8: Identify and Authenticate Access to System Components
You can assign unique identification numbers to each individual in your system, allowing you to monitor and trace all known authorized users. This applies to all systems in the payment infrastructure, including POS accounts, admin accounts, and anything that stores cardholder data.
- Define and implement an official policy for identification management on all system components.
- Assign every user a unique ID or username before granting them access to systems containing cardholder data.
- Authenticate users using one or more methods, including something you know (like a password), something you have (like a token), or something you are (like a biometrics scan).
- Use multi-factor authentication to secure all non-console admin access and remote access to cardholder data environments.
- Make sure all authentication policies and procedures are clearly communicated to all users.
- Don’t use any group or shared IDs as authentication methods.
- Any use of other authentication methods, like smart cards or physical tokens, must be assigned to a specific individual.
- Access to databases containing cardholder data must be restricted, and only database managers can have access.
Requirement 9: Restrict Physical Access to Cardholder Data
This requirement refers to physical hardware and hard copies of data as it pertains to on-site personnel. If they’re physically present on the premises and you have sensitive cardholder data on site, then you must take steps to prevent that data from being compromised.
- Use facility entry controls to monitor movement and limit access to physical systems.
- Create a procedure to know the difference between in-house personnel and visitors (such as a guest pass or ID badge).
- Make sure all visitors are authorized before they enter an area where cardholder data is processed or maintained.
- Use a visitor log to track access and ensure that their credentials either expire or are surrendered upon leaving the premises.
- All stored backups should be stored securely, ideally in an off-site location.
- Maintain strict access controls over the distribution of any of this information.
- Destroy physical access to sensitive data as soon as it’s no longer needed for any business or legal reason.
- Protect all physical devices that capture card data through tampering, substitution, or manipulation (such as period inspections of POS systems).
Monitor and Test Networks Regularly
Both physical and wireless networks connect endpoints and servers within an organization’s payment infrastructure. To prevent these systems from being exploited, you must continuously monitor them to ensure they’re working and test networks to identify any vulnerabilities in your systems.
Requirement 10: Track and Monitor Access to Network Resources and Cardholder Data
Log and track all user activities to help with forensics vulnerability management. By adding a log to all environments, it makes it easier to track and analyze if something is wrong. Without an activity log, it’s much more challenging to determine what caused a breach or compromise in your system.
- Use audit trails to link access to all system components for each user.
- Use automated audit trails to reconstruct events (such as invalid attempts, changes to identification, account deletions, etc.)
- Record audit trails for every event with the type of event, user identification, date, time, success or failure indication, even origin, and system components involved.
- Use a time synchronization feature for all system clocks.
- Make sure audit trails are secured and set so they cannot be modified.
- Review logs regularly to identify suspicious activity or anomalies.
- Keep your audit trail history for at least one year, and ensure a minimum of three months of the audit history is immediately available for review.
- Ensure your service providers have a process to timely detect and report critical failures.
Requirement 11: Test Security Systems and Processes on a Regular Basis
As technology evolves, there are constantly new vulnerabilities being discovered. Regular testing is crucial to see if your system has new vulnerabilities that previously were not known—especially when changing system configurations or deploying new software to your environment.
- Create a process to test the presence of wireless access points.
- Run internal and external network vulnerability scans at least once per quarter and after every significant network change.
- Create an internal method for penetration testing and run internal penetration tests at least once per year and after every significant network change.
- Use intrusion detection and prevention techniques on your network.
- Monitor all traffic and critical access points in the cardholder data environment.
- Alert personnel if a compromised network is suspected.
- Set up a change detection system if there’s an unauthorized modification to crucial system files.
Maintain an Information Security Policy
An information security policy is the backbone for protecting your entire organization. It helps set the standards for all employees and users—explaining their roles, duties, and responsibilities as it relates to cardholder data and how they must protect it.
Requirement 12: Maintain a Policy That Addresses Information Security
Everyone in your organization must be aware of the security policies, and have access to it.
- Create, publish, and maintain a clearly defined security policy.
- Review your security policy at least once per year and make changes accordingly.
- Establish a formal risk assessment process that’s performed on a regular basis to identical critical assets, threats, and vulnerabilities.
- Create usage policies for all critical systems to define what’s considered “proper use.”
- Make sure that the security policy clearly defines the security responsibilities of all personnel and service providers.
- Appoint an individual or team to be responsible for information security.
- Create a formal security awareness program to educate and inform personnel about cardholder data security policies.
- Formally screen personnel prior to hiring to help minimize the risk of internal threats.
- Make sure all service providers put in writing that they’re responsible for all cardholder data that they possess, store, or transmit.
- Create an incident response plan.
- Make sure service providers perform document reviews at least once per quarter.
Final Thoughts
PCI DSS compliance can feel a little overwhelming. While the language used by the PCI Data Security Standards Council might raise some eyebrows and be tough to understand at first, it’s important to recognize that they’re using broad enough terms to help cover the billions of card transactions that get processed every day.
Lots of this stuff is common sense, and you should be able to rely on your merchant services provider to help ensure your technology and systems are updated and secured with PCI compliance standards.